ING.com security
Background
ING provides the following general information to answer any concerns that you may have around the security of the internet, including online transactions. More specific information should be available from your bank, broker or ING representative.
ING makes every effort to provide optimal security of your data and of all transactions; for us protecting our clients is just good business. However hard we work there are risks online, and you can take some action to protect yourself. Here we provide some information to help you.
Latest key security issues
From time to time we will provide information on security related news items that we feel you should be aware of. These security updates will be presented on this page.
Bank Guarantee Fraud
Bank guarantee fraud involves bogus investment schemes that promise you quick riches if you invest in a fund that buys bank guarantees issued by prime banks such as ING.
The fraudsters will invite you to invest and will tell you that the bank guarantees will be bought at a discount and sold shortly afterwards at a huge profit. They will try to make the schemes appear legal and legitimate by showing you complex, sophisticated documents that appear to be official. They may tell you, falsely, that your investments will be secured by letters of credit, bank guarantees or other guaranteed certificates backed by the world’s major banks. They will claim that you will make high profits if you invest large sums in their schemes. As soon, however, as you part with your money, it will disappear – along with the investment company.
Do not respond to these emails. They are part of a fraud and you will not receive any of the promised money.
Fake job postings
A known recruiting scam, claiming to represent companies, invites people to apply for a “job” that turns out to actually be a form of money laundering. These types of employment offers are in no way associated with ING Group.
As criminals become more sophisticated, these e-mails may include your name and other personal information, making it more difficult to detect them as fraudulent.
If you receive any e-mails please don’t respond to them. If you have already responded, consider reporting the incident to the police.
Phishing
A phishing attack is an online fraud technique which involves sending official-looking email messages with return addresses, links and branding that all appear to come from legitimate banks, retailers, credit card companies, etc. Such emails typically contain a hyperlink to a spoof website and mislead account holders to enter customer names and security details on the pretence that security details must be updated or changed. Once you give them your information it can be used on legitimate sites to take your money.
It is important that you are suspicious of emails asking for your information; see more on ING’s standard email practices below.
Imitation of ING websites and Apps
ING monitors the internet to find imitation websites and apps, which are often the first step made by phishers. We then work with the appropriate international authority to get the websites closed down and Apps taken out of the App stores as quickly as possible – sometimes on the same day we find the website or App.
To report phishing attacks please send us an email.
Advanced Fee Fraud
You may already have heard of ‘advanced fee fraud’, where emails offering large sums of money are sent to thousands of email addresses, but a modest ‘fee’ was required in order to cover legal fees, open an account or pay customs charges. Sometimes the money offered is as a result of a lottery for which you have never bought a ticket. Sometimes the money is held in an account overseas but the account owner cannot access it, they promise a percentage of the money in return for your help. In both cases various fees have to be paid.
Do not respond to these emails. They are part of a fraud and you will not receive any of the promised money.
We place this warning here because we are aware that the criminals carrying out these frauds do on occasion use the name of ING or an ING subsidiary as part of this scam.
ING’s standard practices
ING may communicate with clients by mail on occasion, so how can you tell which mails are from us, and which are fraudulent?
- ING will address you by name in any emails.
- ING will not embed hyperlinks in emails that take you to sites where you must enter your security information.
- ING emails will never ask you to reply in an email with any personal information.
- ING will use state of the art encryption and authentication mechanisms to secure the transactions; these will vary per country so check with your local bank about the processes used.
- ING will never claim your account may be closed if you fail to confirm, verify, or authenticate your personal information via email.
- ING will never claim the need to confirm important information via email due to system upgrades.
If clients have any doubt about any email they have received purporting to be from ING they should contact their bank.
Verifying Websites
Clients must be sure that the site they are entering really belongs to ING, and is a secure site;
Check that your website is secure,
- The URL will begin with https://
OR - The application window will specify that SSL (Secure Sockets Layer) Library.
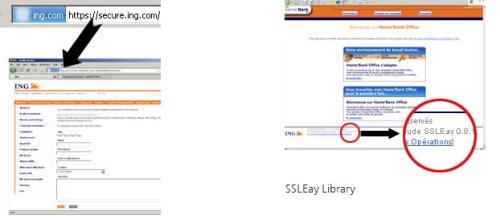
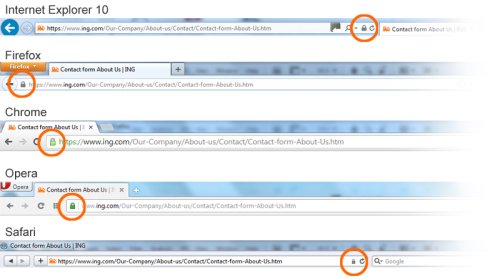
If https, the secure lock icon, a small padlock will appear on the browser in the positions as detailed below:
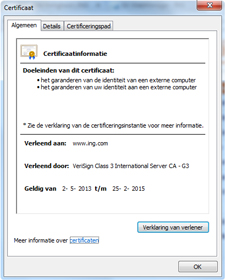
When you click on the icon with the padlock, then a security certificate should appear. The certificate shows who owns the website; it should show the name of your bank. Verify that the data and validity are correct.
We work with well known certification authorities such as Verisign, GlobalSign and Thawte.
If customers have any doubts about a website they should contact their bank.
What can you do to protect yourself from fraudulent apps for smartphones?
Just because an app is in an App Store doesn’t mean that it is a legitimate app. App store owners constantly remove fraudulent apps from the app stores, such as fake antivirus, browsers, and games. Cyber scammers also attempt to impersonate ING products.
Scammers will try any means necessary to trick you into installing a fake app. Criminals use emails and SMS messages that appear to be from a trusted brand, e.g. ING, to trick you into downloading applications that will compromise your data. Sometimes fake apps will pose as security updates, and clicking on the links may also lead to your information being stolen.
Only download apps from official sources. Before downloading any app, do some research. How many times the app has been downloaded? A wildly popular app is a telltale sign of a good app. Read app reviews, look at the developer, and do a search online.
If you receive an unexpected SMS, a strange alert or notification, or unusual requests from ING or other familiar brand, beware: criminals may be trying to install a fraudulent app. Use caution with any link delivered to you and always read the message first. Instead of using the link supplied in the message, go directly to the website or app-store you normally use and log into your account the way you would normally do.
Protect Yourself
Take care of your personal information
Your account numbers, customer Number, PIN (password), memorable date and customer identification number are the keys to your account. Never write them down, give them to anyone else or include them in an e-mail. Destroy documents containing personal information securely, and be very cautious in posting personal details to social networking sites on the internet, as criminals can use this information to commit fraud. Remember that protecting your Customer Number, PIN, passwords and security details is your responsibility.
Take care of your computer
- Update your computer by installing the latest software and patches, to prevent hackers or viruses exploiting any known weaknesses in your computer
- Install and update virus protection, to protect against viruses corrupting your computer and to prevent hackers installing Trojan viruses on your computer
- Install and update anti-spyware tools.
- Install and update personal firewalls
- Use only programmes from a known, trusted supplier.
Beware of Spam Emails
- Use a spam filter to avoid even seeing these messages
- Never respond to a spam message, your email address is then recorded as live and the spam will increase.
- Should you read a spam message remember: if it sounds too good to be true, it probably is too good to be true.
Reporting vulnerabilities
At ING, the safety of internet banking and the continuity of our online services are our top priorities. Our specialists work continuously to optimise our systems and processes. Despite the effort we put into the security of our systems, technical vulnerabilities could still be identified.
Have you found any vulnerabilities in our systems? Please help by reporting these vulnerabilities to us, so that we can improve the safety and reliability of our systems.
The official channel for reporting vulnerabilities is the Intigriti platform.
For all necessary details of ING Responsible Disclosure programme terms please visit https://app.intigriti.com/company/programs/ing/ing-responsible-disclosure/detail
More info
- The US Federal Trade Commission provides information here on how to avoid phishing scams
- The Anti-Phishing Working Group provides statistics on phishing attacks and advice for individuals and companies.
